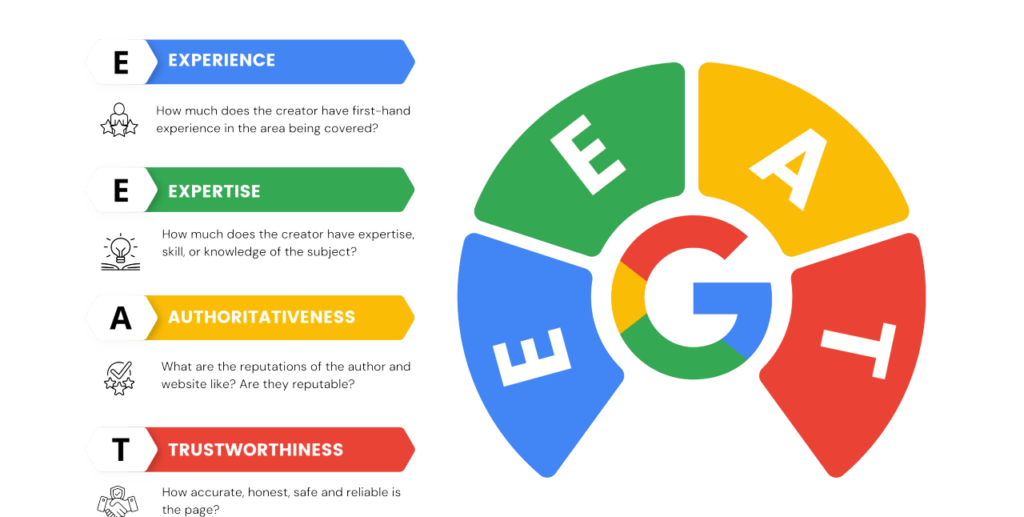
Information technology (IT) security is a major problem for people, companies, and organizations in today’s digital environment. The risk of cyber threats and data breaches rises as technology develops and more data is kept online. Protecting sensitive data from unauthorized access, use, disclosure, disruption, alteration, or destruction requires strong IT security.
What is Information Technology Security?
IT security, also known as cybersecurity, refers to the practices, technologies, and processes designed to safeguard digital information, computer systems, and electronic data from various
types of threats. These threats can be intentional, such as hacking and viruses, or unintentional, like hardware failures and natural disasters.
Key Components of IT Security
1. Confidentiality: Protecting sensitive information from unauthorized access.
2. Integrity: Ensuring data accuracy and completeness.
3. Availability: Guaranteeing access to data and systems when needed.
4. Authentication: Verifying user identities and access rights.
5. Authorization: Controlling user access to resources and data.
Types of IT Security Threats
1. Malware: Viruses, worms, trojans, and ransomware.
2. Phishing: Social engineering attacks via email or phone.
3. Denial of Service (DoS): Overwhelming systems with traffic.
4. SQL Injection: Exploiting vulnerabilities in databases.
5. Insider Threats: Authorized personnel misusing access.
Best Practices for IT Security*
1. Implement Firewalls and Antivirus Software
2. Use Strong Passwords and Multi-Factor Authentication
3. Regularly Update Software and Systems
4. Conduct Security Audits and Risk Assessments
5. Educate Users on Security Awareness
Understanding IT Security
Information technology security is the collection of tactics, procedures, and tools used to protect information networks. This wide area of study covers safeguarding data, networks, and computer systems from dangers like malware, phishing, and hacking. Ensuring the confidentiality, integrity, and availability of data requires IT security.
Information technology security is a vital aspect of protecting digital information and systems from various threats. By understanding the components, types of threats, and best practices, individuals and organizations can take proactive measures to safeguard their sensitive data and prevent cyber attacks.
Here are some FAQs on Information Technology (IT) Security:
Q:1 What is Information Technology (IT) Security?
A: IT Security refers to the practices, technologies, and processes designed to protect digital information, computer systems, and electronic data from unauthorized access, use, disclosure, disruption, modification, or destruction.
Q:2Why is IT Security important?
A: IT Security is crucial to protect sensitive information, prevent financial loss, maintain confidentiality, integrity, and availability of data, and ensure business continuity.
Q:3 What are common IT Security threats?
A: Common threats include malware, phishing, ransomware, viruses, Trojan horses, spyware, adware, SQL injection, cross-site scripting (XSS), and denial-of-service (DoS) attacks.
Q:4 What is a firewall, and how does it work?
A: A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
Q:5 What is encryption, and how does it work?
A: Encryption is the process of converting plaintext into unreadable ciphertext to protect data confidentiality, integrity, and authenticity.
Q:6 What is the difference between a virus and a worm?
A: A virus requires human interaction to spread, while a worm can spread automatically without human intervention.
Q:7What is phishing, and how can I avoid it?
A: Phishing is a social engineering attack that tricks users into revealing sensitive information. Avoid suspicious emails, verify sender identities, and never click on unfamiliar links.
Q:8 What is two-factor authentication (2FA), and how does it work?
A: 2FA adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone or a biometric scan, in addition to a password.
Q:9 How often should I update my software and operating system?
A: Regularly, as updates often include security patches and bug fixes to protect against known vulnerabilities.
Q:10 What is a vulnerability, and how is it different from a threat?
A: A vulnerability is a weakness in a system or software, while a threat is an exploit or attack that takes advantage of a vulnerability.
Q:11What is the role of an IT Security professional?
A: IT Security professionals design, implement, and maintain security measures to protect computer systems, networks, and data from cyber threats.
By understanding these fundamental concepts and best practices, you can better protect yourself and your organization from cyber threats and maintain the confidentiality, integrity, and availability of your digital information.